
Group Therapy 221 with Above & Beyond and Myon
Group Therapy 221 with Above & Beyond and Myon Subscribe to our channel: http://po.st/ytab iTunes Podcast: http://bit.ly/ABGTpodcast http://www.aboveandbeyon…


Group Therapy 221 with Above & Beyond and Myon
Group Therapy 221 with Above & Beyond and Myon Subscribe to our channel: http://po.st/ytab iTunes Podcast: http://bit.ly/ABGTpodcast http://www.aboveandbeyon…


XKCD: All Comics
Comic Title: Listening
Comic Number:1807
Comic Alt-Text:
Sure, you could just ask, but this also takes care of the host gift thing.https://www.facebook.com/xkcdallcomics/photos/a.1629809743996250/1731131747197382/?type=3

![]()
https://www.youtube.com/watch?v=TiHYQFZgN4I
Hiroyuki Sawano – 1 Hour Attack on Titan OST – Epic Music ▬▬▬▬▬▬▬▬▬▬▬▬▬▬▬▬▬▬▬▬▬▬▬▬▬ ►Composed by Sawano Hiroyuki ►Anime: Attack on Titan, Shingeki no Kyojin,…

With the CIA and the State Department (Hillary) out of the picture, and with their covert operation to arm and finance “moderate” jihadist rebels having ended ..
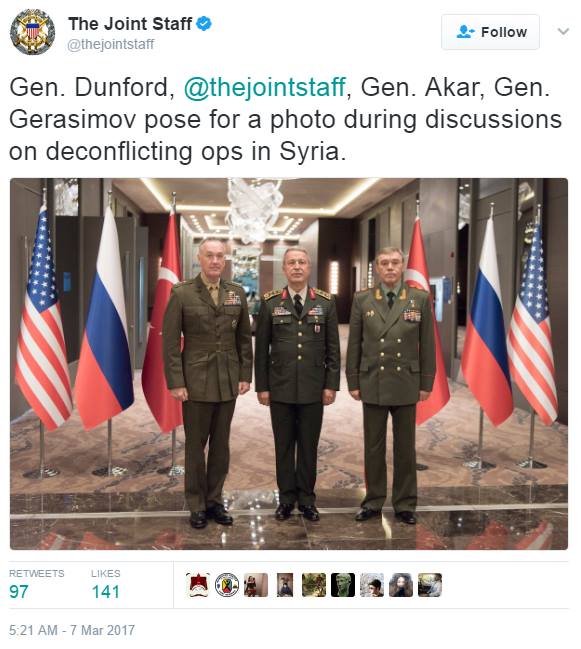
US, Turkish, and Russian generals discussing “deconflicting” operations in Syria ..
Gen. Dunford, @thejointstaff, Gen. Akar, Gen. Gerasimov pose for a photo during discussions on deconflicting ops in Syria. pic.twitter.com/DPJv4aEBh6
— The Joint Staff 🇺🇸 (@thejointstaff) March 7, 2017
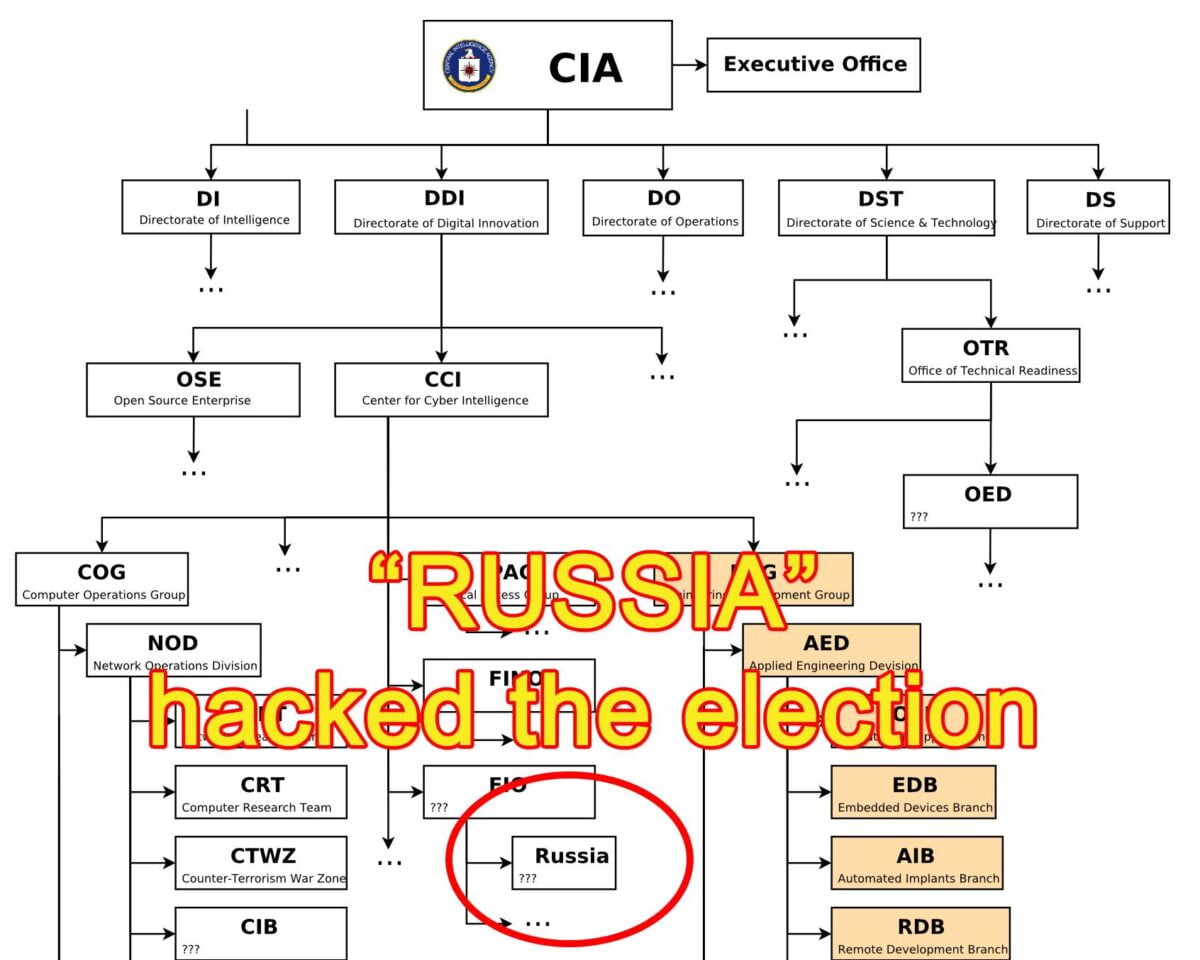


“Russia” hacked the election .. How do we know? Because “they” left behind “their” fingerprints ..
—
“With UMBRAGE and related projects the CIA cannot only increase its total number of attack types, but also misdirect attribution by leaving behind the ‘fingerprints’ of the groups that the attack techniques were stolen from”
WikiLeaks: CIA hacking group ‘UMBRAGE’ stockpiled techniques from other hackers
Practice would have allowed CIA to leave behind ‘fingerprints’ of other groups.

![]()
“As I was concerned for our own products, I began rummaging around the “Network Devices Branch (NBD)” tool-sets looking for Juniper-specific attacks and implants, of which there appear to be none (further review is of course required to confirm this). What I did find, however, was that the vast majority of them were targeting Cisco equipment.”
CIA Hacking Tools in review: Cisco was a primary target
As I’m sure news sites will be picking this up shortly, I’ll try and be brief today and update this post later with more detailed information as I dig
https://www.linkedin.com/pulse/cia-hacking-tools-review-cisco-primary-target-craig-dods

![]()
https://www.youtube.com/watch?v=DjDzyAny90w
“Wikileaks’ Vault7 Reveals Massive Spying Program on Americans”
Wikileaks’ Vault7 Reveals Massive Spying Program on Americans
Winship on another level. Visit us at http://ibankcoin.com. Indeud.


“Recently, the CIA lost control of the majority of its hacking arsenal including malware, viruses, trojans, weaponized “zero day” exploits, malware remote control systems and associated documentation. This extraordinary collection, which amounts to more than several hundred million lines of code, gives its possessor the entire hacking capacity of the CIA. The archive appears to have been circulated among former U.S. government hackers and contractors in an unauthorized manner, one of whom has provided WikiLeaks with portions of the archive.”
Vault7 – Home
If you need help using Tor you can contact WikiLeaks for assistance in setting it up using our simple webchat available at:
CIA CCI are amoral black hat hackers who exploit any and all consumer electronics.